Explain Different Types of Attacks in Information Security
More than 71 of targeted attacks involve the use of spear phishing. There are different types of password attacks like brute force attacks dictionary attacks and keylogger attacks.
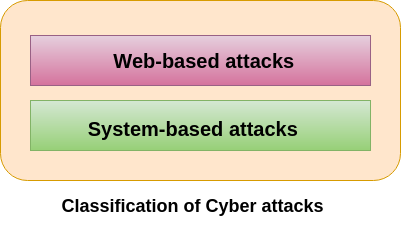
Types Of Cyber Attacks Javatpoint
Network attacks are unauthorized actions on the digital assets within an organizational network.

. The most common are TCP SYN flood attack teardrop attack smurf attack ping-of-death attack and botnets. An active attack has the potential to cause major damage to an individuals or organizations. There are two types of attacks passive attacks and active attacks.
Classification of Security attacks. Computer viruses are one of the most common network security attacks that can cause sizeable damage to your data. All the main seven kinds of networks attacks namely Spoofing Sniffing Mapping Hijacking Trojans DoS and DDoS and Social engineering are described in detail.
It is a form of attack wherein a hacker cracks your password with various programs and password cracking tools like Aircrack Cain Abel John the Ripper Hashcat etc. A security threat is a malicious act that aims to corrupt or steal data or disrupt an. There are two types of attacks Passive attacks and Active attacks.
The security attacks are classified into 2 types 1 Active attacks. Information security attacks can be classified into the below types. Below we are discussing some web-based attacks.
Keep in mind that the security of a network is as strong as its weakest link. Snooping on data eavesdropping is simple examples of passive attacks. A passive attack is one that does not affect any system although information is obtained.
Will help to Understand the threats and also provides information about the counter measures against them. Whereby a data is introduced into a DNS resolvers. Social engineering is a type of password attack that Data Insider defines as a strategy cyber attackers use that relies heavily on human interaction and often involves tricking people into breaking standard security practices Other types of password attacks include accessing a password database or outright guessing.
It is the attack in which some data will be injected into a web application to manipulate the. One entity pretends to be a different entity. Methods of Cyber Attacks 1.
DNS Spoofing is a type of computer security hacking. These attacks are not very dangerous as they do not cause any modification to the data. Although the terms security threat security event and security incident are related in the world of cybersecurity these information security threats have different meanings.
In this attack an attacker exploits the use of the buffer space during a Transmission Control Protocol TCP session initialization handshake. A cyber attack refers to an action designed to target a computer or any element of a computerized information system to change destroy or steal data as well as exploit or harm a network. In an active attack the attacker tries to modify the information.
Malware is a form of application that performs nefarious activities. Perpetrators in network attacks tend to target network perimeters to gain access to internal systems. A good example of this is wiretapping.
Spear phishing is a more sophisticated form of a phishing attack in which cybercriminals target only privileged users such as system administrators and C-suite executives. An attack is one of the biggest security threats in information technology and it comes in different forms. In addition to identifying such attempts anti-spoofing software will stop them in their tracks.
Here we discuss the top 10 networking threats and attacks. The classification of InfoSec Attacks. These attacks are facing by the organization or individuals on a web application or a website.
Passive attacks are not as harmful as they do not cause any altering or modification of data. Different Types of Attacks in Cryptography and Network Security Types of Attacks in Cryptography and Network Security. While there are dozens of different types of.
A type of malware they are unique pieces of code that can wreak havoc and spread from computer to computer. Before going to the receiver the attacker. Detailed descriptions of common types of network attacks and security threats.
Active attacks With an active attack the attacker tries to break into the application directly. Malwares can be used for extortion. Malicious parties usually execute network attacks to alter destroy or steal private data.
There are different types of DoS and DDoS attacks. Thankfully there are different solutions that detect the common types of spoofing attacks including ARP and IP spoofing. Techopedia Explains Attack.
There are two main types of network attacks. Attacks can be divided into two different types. Due to the modification this attack can be easily detected because of visibility.
Cyber attacks have been on the rise in sync with the digitization of business that has become more and more popular in recent years. There are a variety of ways this could be done from using a false identity to access sensitive data masquerade attack to flooding your server with massive amounts of traffic to make your application. Phishing attack accounts for over 80 of reported cyber incidents.
Evolution of Cyber Security. Extra Precautions for Personnel. In Phishing an attacker tricks an unsuspecting target into handing over valuable information such.
TCP SYN flood attack. 4 Man in the Middle Attack. In computer networks and systems security attacks are generally classified into two groups.

7 Types Of Cyber Attacks Targeting You Right Now Data Science Learning Cyber Attack Cyber Security Awareness

Different Types Of Network Attacks And Security Threats And Counter Measures Types Of Network Network Infrastructure Networking

Active And Passive Attacks In Information Security Geeksforgeeks

Top 10 Most Common Types Of Cyber Attacks Cyber Attack Ddos Attack Attack
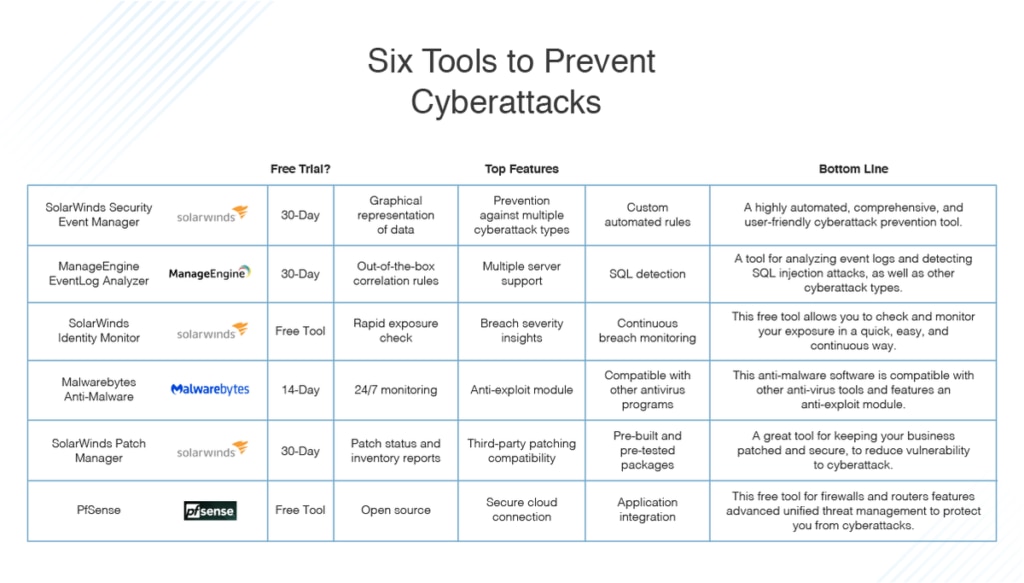
Top 6 Common Types Of Cyberattacks Dnsstuff
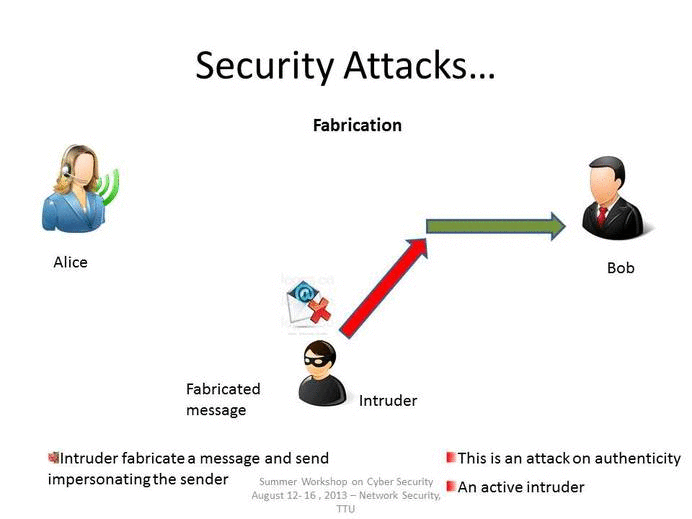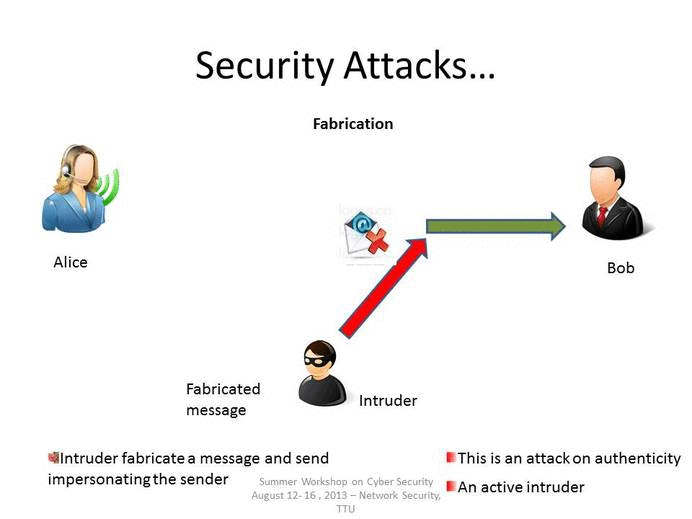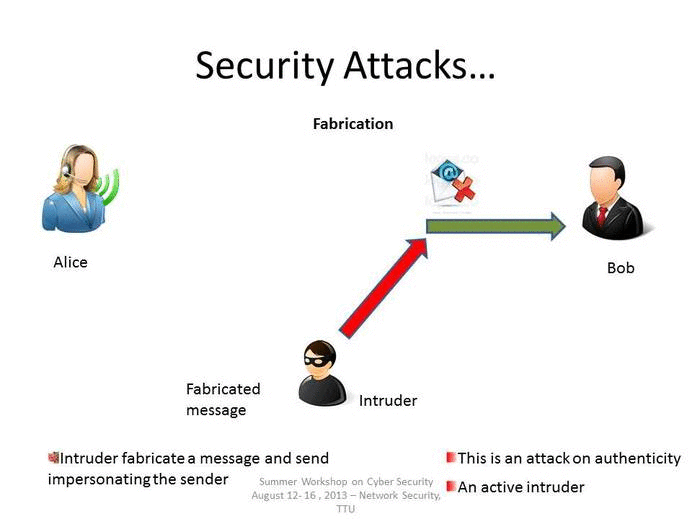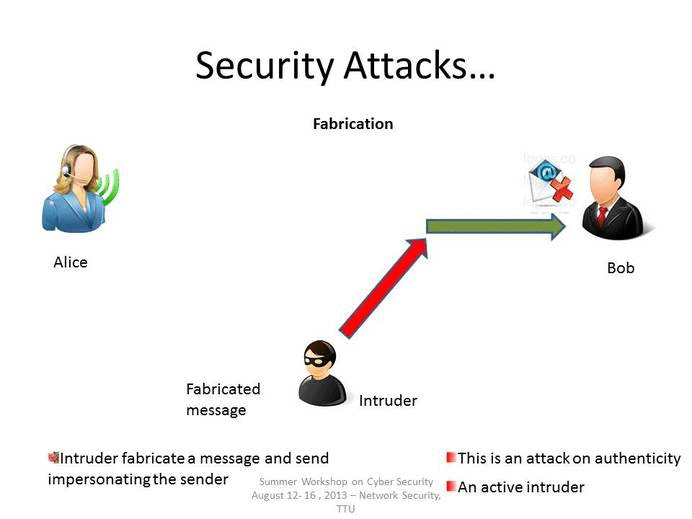
1 4 Attacks Types Of Attacks Engineering Libretexts
Types Of Cyber Threat In 2021 It Governance Uk

Human Firewall Tip 11 Social Engineering Prevention Cyber Security Awareness Cyber Security Awareness
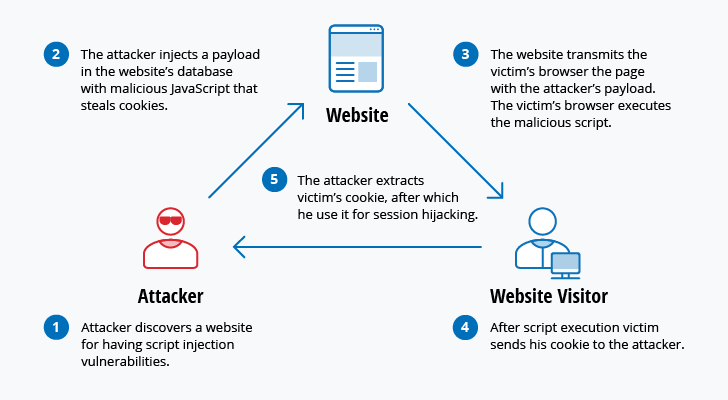
No comments for "Explain Different Types of Attacks in Information Security"
Post a Comment